Over the last decade the cases of cryptojacking has increased, which is a huge concern for crypto miners as it jeopardizes their systems. According to an annual report of 2021, the European Union Agency for Cybersecurity, cryptojacking is the third most common cyber threat. Whereas the expert of Google Cybersecurity Action Team has stated that around 86% of victims of cyberattacks are cloud platforms compromised by cryptojacking.
Criminals find cryptojacking a profitable way of earning cryptocurrency as they do not have to use their own resources to process and generate coins. Saving processing expenses without having to steal directly from victims. Thus, it’s important to educate yourself about threats like cryptojacking and how it works. So, continue reading the article if you want to know more about cryptojacking
What is Cryptojacking?
Cryptocurrencies are based on “blockchain,” which is a distributed ledger that stores all transactions, which gets periodically updated. A complex mathematical process is executed that merges all the recent transactions into a single ‘block.’
To generate new blocks, the cryptocurrency relies on individuals known as “miners” to supply computing power in exchange for which they get rewarded with cryptocurrency. In simple words, miners are those who exchange computational resources for cash.
To execute and compute complex hash puzzles, the cryptocurrency firm hires a team of expert miners who use dedicated computer rigs to generate coins. This activity requires a substantial quality of electricity. For example, the Bitcoin network alone consumes around 73 TWh energy each year.
This is where crypto jacking comes into play: Cryptojackers seek to gain cryptocurrency mining without having to pay for mining equipment or high power bills. Cryptojacking enables hackers to use victims’ resources to mine coins and transfer them to their own wallets without leaving a trace behind.
Malware’s up, ransomware’s down-but not out, and #IoT #malware and #cryptojacking attacks reached record highs. The 2023 SonicWall Cyber Threat Report infographic offers a snapshot of the #cybersecurity industry’s top threats and trends. Get it here: https://t.co/zC0zLbomTl pic.twitter.com/hkIyWySEus
— SonicWall (@SonicWall) May 14, 2023How Does Cryptojacking Work?
Cryptojackers hack the victim’s devices through installed cryptojacking software on the target computer. The software works in the background on the target computer. The software mines cryptocurrency or steal cryptocurrency from target crypto wallets. While the unaware victims continue to use their devices. However, they may notice sluggish performance or delays.
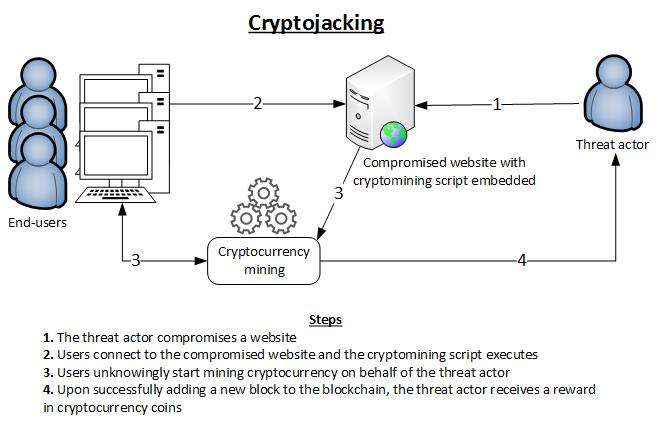
Cryptojackers have two main tactics through which they target the victim’s computer to secretly mine cryptocurrency and some even combine both these tactics.
Download
In this method, the target is encouraged to download and install crypto-mining code on their devices using techniques like phishing. In which the target may get an email attached with a link that seems authentic. Once the link is clicked, it installs crypto-mining software on the target device. While the victim is working on the computer, the script runs in the background.
Injection
In this technique, a script is injected into an advertisement or website that later spreads to multiple websites. When the victim visits a malicious page or the malicious advertisement appears on their browser, the script starts to execute automatically. No code gets saved on the victim’s devices, making it hard to detect.
In both tactics, the virus runs complicated mathematical calculations on the targeted computer and transmits the result to a hacker-controlled website.
Hybrid
To boost profit, sometime hackers may combine both tactics. For example, if 20% of the hundreds of devices that attackers may use to mine coins by running code on the target computers, while 80% could do using the web browser.
To maximize the potential of the attack and its spread over a network, hackers may incorporate several variants of a virus that exploit various vulnerabilities in network protocols. And execute each unit one runs successfully.
Conclusion
Cryptojacking attacks are difficult for the victims to detect. Thus, hackers are making quite profitable using the victim’s system resources. Therefore, taking precautionary measures like periodically updating your operating system and installing anti-virus software is crucial.
Adding ad-block and anti-crypto extension on your web browser is also a smart move. Be mindful about the website you visit and do not link on suspicious looking links and attachments are some basic rule you should follow to ensure a certain level of security from threats.
















