Certainly, public and private keys have become a major part of the cryptocurrency framework. These keys are generated through cryptography. According to findings, cryptography is a technique geared towards the encryption and decryption of information at the heart of a crypto and blockchain. We can thus refer to the keys as a part of the public-key cryptography (PKC) framework. It is worth mentioning that public and private keys come with crypto wallets. With these keys, users are able to send and receive crypto assets without any intermediary. So, we can say the presence of the public and private keys removes the interference of third parties in verification of transactions.
You can learn more about the rudiments of crypto wallets by clicking here.
It has been established that the emergence of these keys ensures that users can send digital assets to strangers without any intermediary. They provide the security framework for transferring crypto assets on the blockchain network. It is worth noting that both public and private keys serve different purposes, but are necessary to complete crypto transactions in a given network. This means a crypto transaction cannot be certified successful without these keys. However, this article will provide insights into both public and private keys and their respective functions.
Public and Private Keys: Introduction
What are Public Keys?
Public keys are those keys that provide enablement for sending a specific crypto asset that can be sent or received. Anyone willing to receive cryptocurrency avails the keys to the sender to aid the transaction. We can define public keys as a cryptographic code that comes with a particular crypto wallet. It is safe to send your public key to anyone. The only thing anyone with the key can do is to leverage it to send you funds. By virtue of this, it is not in doubt that your wallet cannot be prone to exploitation just by sharing your public keys.
According to findings, public keys are usually generated mathematically from private keys. Whenever any funds are sent to a public key it is usually unlocked with the private key. This thus means owners of crypto wallets need to prove that they own the received crypto assets. In a nutshell, we can say public keys offer fundamental security primitives.
These keys serve as the hashed version of a users’ public address. Since they entail a long string of numbers, they are shortened to become public addresses. So, while the private key generates public key, the latter consequently generates public address.
What are Private Keys?
Private keys entail alphanumeric code which helps to authorize transactions and confirm ownership of a given crypto asset. As an integral aspect of a crypto network, these keys and its properties safeguard users from unauthorized access to their assets. This thus means users cannot share their private keys like they do with their public keys.
Meanwhile, you can also get to know how to protect your crypto assets from exploitation here.
This is because anyone who accesses these keys can access the funds in one’s wallet. For those who keep assets in a centralized exchange, the private key is then in the hands of that particular exchange. These exchanges avail custodial wallets which help users to manage their private keys.
Likewise, you can also learn about top crypto exchanges with no KYC here.
However, amid the growing uncertainty with centralized exchanges, like Binance, Coinbase, FTX, and more, many believed non-custodial remains the most credible alternative. Recall that the collapse of FTX, for instance, have heightened doubts in centralized exchanges, with many arguing that one does not own cryptocurrencies if you are not the self-custodian of your private key.
You can also read our review on Coinbase as one of the leading centralized crypto exchanges around.
With non-custodial wallets, users are in charge of their keys. However, the configuration of many of these wallets encodes the private keys in the form of seed phrases for back up. However, private keys take many forms. They include 256 character long binary code, 64 digit hexadecimal code, QR code and Mnemonic phrase.
To read more about custodial and non-custodial wallets, click here.
How Public and Private Keys aid crypto transactions
Certainly, public and private keys are necessary to aid the successful completion of crypto transactions. Understanding the properties of these keys and how they work together is essential in understanding how crypto transactions are carried out. For crypto transactions to complete successfully, it must be digitally signed with a private key. How this is done is not far-fetched.
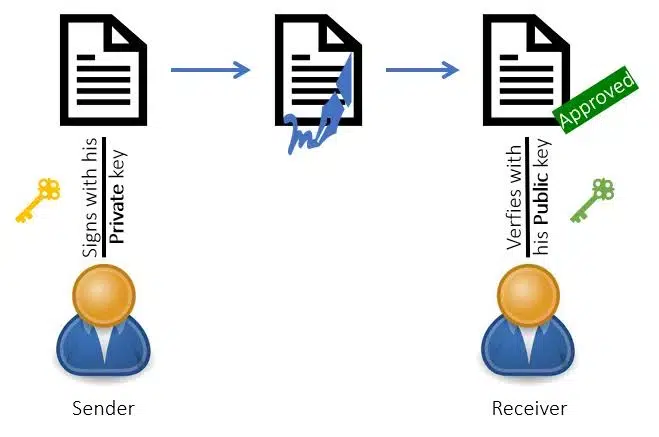
Whenever a transaction is initiated on a crypto wallet, it constructs the details entailing the sender’s address, receiver’s address, amount and other necessary metadata. Afterward, the private keys are harnessed to create a digital signature to confirm the legitimacy of the transaction. Upon the completion of the digital signing, the transaction is consequently transferred to the network for nodes to verify its authenticity.
Protecting your Private Keys
Since you do not control your keys in custodial wallets, you cannot be in charge of protecting them. This thus means any vulnerability on the part of the wallet might lead to the loss of users’ funds. For instance, the financial issues with FTX left its users with an overall loss of $6 billion.
But, as for non-custodial wallets, users play a huge role by protecting their keys. To protect the keys, users must not share their private keys with anyone. Also, they must use a recovery phrase to back up your private keys. By doing so, users will be able to safeguard their funds.
Public and Private Keys: Conclusions
We have established the relevance of public and private keys in ensuring the successful completion of crypto transactions. Certainly, both keys work together to make this possible. While users can share their public keys to people, they must protect private keys to safeguard their assets. Any vulnerability on the private keys lead to loss of assets in users’ wallets. By virtue of this, users must be careful with their keys.