Quantum computing is no longer a distant theoretical concept; it’s quickly becoming a practical reality. As this technology advances, it poses a significant threat to current cryptographic systems which are foundational to blockchain technology.
- The Threats of Quantum Computing to Blockchains
- Developments of Quantum-Resistant Cryptography
- Quranium’s Quantum Proof Security Capabilities: A Case Study
- Quantum-Resistant Core: SPHINCS+ and WOTS+
- Hybrid Dual Layer Architecture
- Proof of Respect (PoR) for Collaboration and Fairness
- “Point of Truth” Mechanism for Consistency
- Integration of IoT
- Why is Quranium the Answer to Quantum Proof Security in Blockchain?
- Conclusion
The importance of quantum proof security in blockchain cannot be overstated. Quantum computing threatens classical algorithms like RSA and ECC that support secure communication. Implementing quantum-resistant algorithms ensures blockchain’s data integrity and security to safeguard against quantum attacks and preserving the technology’s immutability, security and reliability.
Vitalik Buterin, co-founder of Ethereum, has been vocal about the potential threats posed by quantum computing of blockchain technology. Additionally, CEO of Post-Quantum, Andersen Chen, has said, “Within three years, there is one in seven chances that quantum computers will break the most used computer encryption systems; this number goes as high as 50% by 2031.”
In this article, we’ll dive into the importance of quantum proof security in the blockchain sector and discuss the case study of Quranium’s pioneering approach to quantum-resistant distributed ledger technology (DLT).
The Threats of Quantum Computing to Blockchains
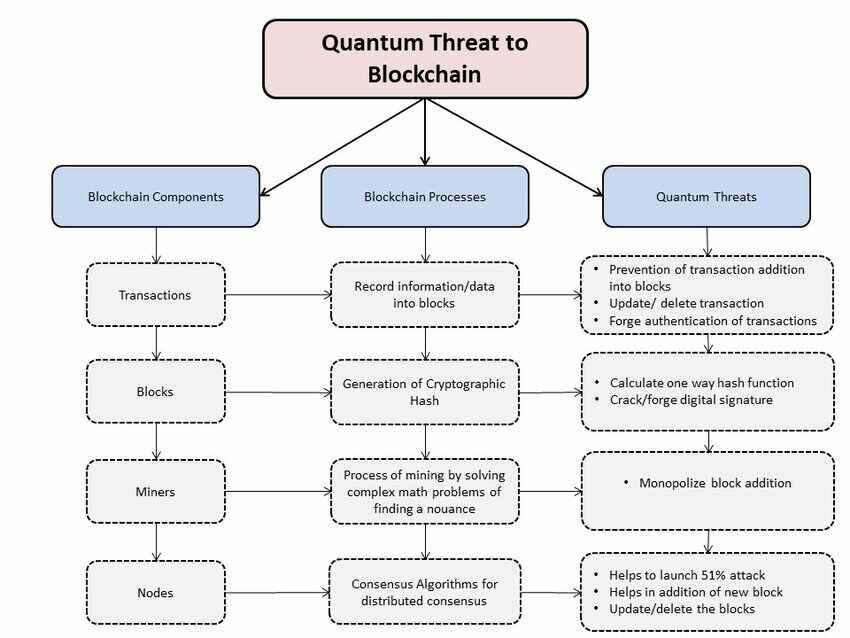
Quantum computers are like super powerful computers that can solve problems that are too complex for regular computers. This power comes from quantum bits (or qubits) which can perform many calculations at once. A big worry is that these computers could one day break many of the encryption methods that keep our data safe.
For instance, the Elliptic Curve Digital Signature Algorithm (ECDSA) is the most widely used cryptographic algorithm implemented by blockchains today. It has a severe weakness to a quantum attack because it was designed to be used in pre-quantum computers which could be exploited by hostile actors ranging from market manipulators to states that are anti-crypto.
Quantum computers leverage quantum mechanics principles such as superposition and entanglement to solve complex problems exponentially faster than classical computers. Undoubtedly, it poses a threat to cryptographic systems that secure blockchain transactions. Curious as to how?
Impact on Public-Key Cryptography
Quantum algorithms like Shor’s algorithm can break widely used public-key cryptographic methods leading to potential unauthorized access and transaction forgery – clearly showing the need for quantum proof security.
Impact on Symmetric Key Cryptography
While symmetric key cryptography is more resistant, algorithms like Grover’s can reduce the security of these keys and necessitates longer keys for maintaining security.
Also, it is important to know the risks posed by quantum computers to network protocols–which can be categorized into two primary areas–Compromised Encryption Algorithms & Undermined Digital Signatures.
Firstly, quantum computers have the capability to compromise the encryption algorithms integral to these protocols, literally putting data confidentiality and integrity in jeopardy. Encryption methods that rely on the complexity of mathematical problems become vulnerable to quantum algorithms like Shor’s algorithm.
Secondly, quantum computers can undermine the authenticity and non-repudiation provided by digital signatures – essential for verifying the source and integrity of digital documents and transactions.
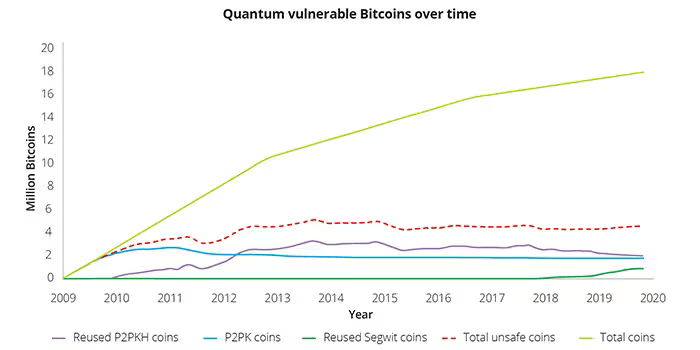
To address these vulnerabilities, researchers have been exploring post-quantum cryptographic (PQC) solutions that are resistant to such attacks.
Developments of Quantum-Resistant Cryptography
Significant efforts are underway to develop quantum-resistant cryptographic algorithms. The U.S. National Institute of Standards and Technology (NIST) has selected several algorithms for post-quantum cryptographic standards.
NIST’s Post Quantum Cryptography Standardization
NIST has chosen four algorithms as the basis for post-quantum cryptographic standards, viz;
- CRYSTALS-Kyber
- CRYSTALS-Dilithium
- SPHINCS+
- FALCON
But mind you, transitioning to quantum-resistant cryptography involves technical, logistical and educational challenges. And amidst the rising challenges posed by quantum computing, Quranium emerges as a visionary platform which is setting new standards in quantum proof security for the blockchain space. Let’s explore Quranium’s unique approach to quantum-resistant cryptography and its innovative architecture.
Quranium’s Quantum Proof Security Capabilities: A Case Study
Quranium is an innovative blockchain platform designed to address both current and future challenges in DLT and specifically it focuses on mitigating the risks posed by quantum computing to traditional cryptographic methods.
Let’s talk about how exactly Quranium faces these challenges head on–
Quantum-Resistant Core: SPHINCS+ and WOTS+
Quranium integrates the NIST-approved hash-based post-quantum signature scheme–SPHINCS+ algorithm.
SPHINCS+ implements stateless, hash-based signatures for PQC. This design avoids well-understood cryptanalysis of lattice-based and code-based schemes by Shor’s Algorithm, ensuring long-term security in the quantum era. Additionally, its stateless nature eliminates key management overhead and reduces human error. The scheme offers flexibility by adjusting signature size based on the desired security-speed trade-offs.
Quranium further secures its platform with WOTS+. As its name implies, it is designed for a single use per key pair so that each signing key is used to sign only one document or transaction.
Why is it important though? Well, this significantly complicates potential attack vectors and enhances the platform’s resilience against sophisticated cyber attacks.
Hybrid Dual Layer Architecture
Quranium tackles the “blockchain trilemma” – the challenges of achieving scalability, security and decentralization simultaneously – with a hybrid architecture. And so, by integrating traditional blockchain with a BlockDAG system, Quranium provides a more scalable and efficient platform with high level security and ensure quantum proof security.
Core Layer (Proof of Work for Security)
Providing a strong foundation for the entire network, the core layer of Quranium’s architecture is renowned for its supreme security and resistance to attacks as it ensures immutability and integrity of the ledger.
Crust Layer (Speed & Scalability with BlockDAG)
If a blockchain is a straight line of blocks, a BlockDAG is like a web. Each block can be connected to multiple blocks instead of just one – ultimately more transactions being processed in parallel, speeding up the verification process. It’s particularly useful in a system like PoR where many participants might be adding information at the same time.
Proof of Respect (PoR) for Collaboration and Fairness
Quranium employs a unique consensus mechanism called Proof of Respect that prioritizes the quality and helpfulness of contributions over raw computational power. Clearly, it promotes a collaborative and equitable network environment where honest participation is rewarded.
By integrating PoR within the BlockDAG structure, Quranium achieves two crucial goals.
- First, it prioritizes network security by disincentivizing malicious activities as they won’t yield any rewards.
- Second, it democratizes the process of validation and block creation making the network more inclusive.
“Point of Truth” Mechanism for Consistency
Quranium’s architecture periodically creates a “Point of Truth” block within the crust layer every half hour which acts as a reference point for all preceding blocks so that the subsequent blocks anchor to this point rather than the entire chain of blocks.
Integration of IoT
Quranium is designed to securely integrate Internet of Things (IoT) devices to its network and by using quantum-resistant DLT, Quranium can provide a secure environment for these devices.
Why is Quranium the Answer to Quantum Proof Security in Blockchain?
Quranium presents a compelling solution for blockchain security in the face of potential threats from quantum computing. Perhaps, its core defense lies in the PQC capabilities of SPHINCS+ and WOTS+. Beyond quantum-resistance–
- Quranium’s architecture mitigates the risk of Long Range Attacks (LRAs) and reduces the feasibility of “Nothing at Stake” issues by making it computationally expensive and unprofitable to support multiple blockchain histories.
- While the reputation and contribution-based PoR model incentivizes validators to act honestly and ties their ability to earn rewards to their behavior, Quranium employs an innovative anti-bribery mechanism where users staking Quranium coins for smart contract engagement see the network autonomously increase the stake pool which make it prohibitively expensive for attackers to accumulate a controlling stake.
- Additionally, Quranium supports high-speed microtransactions and secure machine-to-machine interactions.
- Lastly, by being built from the ground up with quantum proof security in mind, Quranium is better positioned to adapt to future technological advancements and security threats.
Quantum computing presents both unprecedented opportunities and formidable challenges. As quantum computing strides toward ‘Q-day’, the imperative for quantum proof cryptographic solutions becomes non-negotiable. Embracing quantum-resistant algorithms is not merely a defensive measure but a forward-looking strategy to ensure security and integrity of digital infrastructures.
Kapil Dhiman, Co-founder and CEO, Quranium
Conclusion
Quantum computers are coming and anyone interested in adequately securing their data must start looking to the future now.
The specter of quantum computing casts a long shadow over the world of blockchain. Current cryptographic methods, the bedrock of blockchain security, are vulnerable to being shattered by these powerful machines, threatening the very foundation of trust and immutability that blockchain promises.
Here’s where Quranium emerges as a beacon of hope, taking a multi-pronged approach to combat the quantum threat. As blockchain technology ventures into uncharted territory, Quranium’s commitment to quantum proof security and innovative architecture positions it at the forefront of securing the blockchain frontier.