With the advent of Bitcoin, Blockchain technology started its footprint in 2009, hoping for a decentralized digital future with a secure way to execute, record, and verify transactions. Over time, blockchain technology expanded and evolved into many other currencies. The wider it grew, the more vulnerabilities were created and exploited by the bad actors.
The essence of Blockchain is security and protection. Despite this, it is susceptible to hackers and bad actors. There are various types of attacks that the bad actors can make. Out of them, 51% attack is the one which is more talked about and sensitive, among others.
Introduction to Blockchain and its Security
Blockchain is not just the name of cryptocurrency; it is an entirely wide industry that has created many industries, applications, and markets. The promise of enhanced security, transparent distributed ledgers, recording effectiveness, and efficiency builds the entire blockchain structure.
Blockchain offers solutions to various sectors, including gaming, trading, health, and finance. The predominant systems used in Blockchain are Proof of Work (PoW) and Proof of Stake (PoS), which have pros and cons.
In Proof of Work (PoW), miners solve complex mathematical problems by finding the output hash value. Miners use many resources to find the value resulting from the hash function. The more complex the problem is, the more computing power and resources it will utilize. The validators verify the solution provided by the miner(s). Bitcoin is the leading coin that uses PoW.
In Proof of Stake (PoS), the keys are in the hands of the validator; here, validators are selected based on the amount of crypto they stake. The more the stake, the more authority they have to validate.
PoS was introduced to enhance security and reduce the computation cost. ETH 2.0 is the most prominent coin which is transforming itself into PoS.
Want to know more about PoW and PoS? Here are the detailed guidelines
What is a 51% Attack?
A 51% attack means that the bad actor can hijack most of the network and spend the coin illegally multiple times. In other words, It is the majority control of a miner or a Group on the blockchain network.
Altcoins with poor controls are more susceptible to this type of attack.
51% Attack Working Mechanism
In normal cases, miners add blocks publicly to the blockchain. However, the bad actor with malicious intent may start adding blocks to his private portfolio instead of broadcasting it publicly. Accumulation continues until the blockchain stake reaches over 50%.
How Does This Attack Take Place?
Hacks intending to execute a 51% attack will try to accumulate more mining power. A single entity might be working to add dominance, or even multiple miners will join to consolidate the miners’ power and influence the hash rate. Here, the coins with low market cap and vulnerable security will be the victims, as it is convenient for the bad actors to purchase the required hash power of a small coin.
Here is a simple example: I bought a bicycle online using a newly launched 200 meme coin, and the crypto is being sent to that online vendor. If I perform a 51% attack on that meme coin, I can reverse the transaction and get the meme coin and the bicycle. I can spend that coin twice.
Most Famous Past Case
In May 2018, a $18 Million hack occurred on Bitcoin Gold (BTG), a sister coin of Bitcoin. The attack turned the worst security fear into reality by switching theory into reality. This attempt was tried using high-level computing power to influence the hash rate. According to the Bitcoinist, “The attacker sends a particular number of BTG tokens to an exchange, trades them for another coin, and makes a withdrawal.
The hacker returns those same coins to their wallet, hence the double-spending problem. Thus, the attacker can spend and hold the same coins simultaneously. Looking at the image above, if all 76 transactions were part of the hack, the hacker has stolen about $18 million based on the current BTG price.”
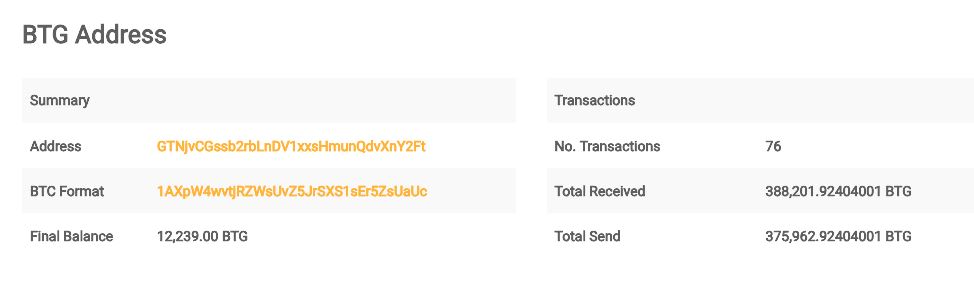
In response to the attack, BTG developers applied a ‘Hard Fork’ update to help restore the investors’ confidence, market reputation, and value. The Ethereum network also launched a similar update.
Did Bitcoin Gold (BTG) Face Another 51% Attack After This?
The short answer is ‘Yes’. However, this time, the 51% attack was not that successful. It was retaliated against and stopped by the developers. Total loss due to this organized attack was expected to be only $70,000. The crypto community appreciated the fightback as it safeguarded the overall reliability and trust belief in the crypto ecosystem.
Is 51% Attack on Bitcoin Possible?
In theory, it is ‘Yes’ but practically ‘No.’ The reason is the size of Bitcoin’s market cap. Due to the enormous size of the coin, it is also impossible to acquire enough hash power to overtake more than 50% level. Although Bitcoin works on Proof of Work (PoW), it is considered vulnerable due to its security controls and measures, immense size, and capability to grow even bigger. A single entity cannot take over its mining hashrate.
Even if someone intends to initiate a 51% attack on Bitcoin, it will be costly to an unmanageable level for anyone.
How Can a 51% Attack Be Prevented?
One of the ways to prevent a 51% attack is to prevent using the PoW algorithm. PoW consumes more electric power and creates a security risk for new or small coins.
The other way is the increasing network growth. The wider the coin grows and the more nodes are connected, the more difficult it is for the bad actors to control its hash rate.
Updating security controls, increasing network size, and keeping the checks on the network are the most visible preventive measures that need to be made to protect the cryptocurrency.
Future of Blockchain Security
With the evolving trends in blockchain development, the concerned cybersecurity teams are also upgrading their advancements.
Quantum Resistant Ledger (QRL)
QRL is developed using the quantum cryptography model, a method of premium data encryption between two parties. This model will enable secure blockchain transactions and help prevent all cyber threats, including 51% attack.
Regulatory Security Compliance
Every finance institution has to comply with certain security standards given by the regulator. In the coming future, with the mainstreaming of blockchain, it has to be compatible with the governments and regulatory bodies to operate at the national or global level.
Conclusion
51% attack is the biggest nightmare for blockchain developers and adopters. Researchers must extensively investigate the threat, and developers should swiftly create response mechanisms to uphold the trust and reputation of the blockchain ecosystem. The vulnerability of a single blockchain is a symbol of an unsecure network, which can also lead to possible attacks on other chains. Adapting the security protocols per developing blockchain technology can keep the security threats in control.
















