Fake profiles are eroding trust in professional networks. These profiles are a growing problem on platforms like LinkedIn, with nearly 89 million fraudulent accounts thwarted in 2023 alone.
LinkedIn marketing strategist and CEO of Judi Hays, Inc., emphasizes the harmful impact of these profiles, quoting, “Fake profiles not only waste valuable time and clog your newsfeed but also expose you to scammers, putting both your personal and network security at risk.”
While professional networks use various measures to combat this issue, such as verification processes and community reporting mechanisms, increasingly sophisticated fake profiles challenge these methods.
One potential solution to this problem is the adoption of decentralized identity systems, which can enhance verification processes while preserving user privacy.
The role of decentralized identity in professional networks is to facilitate user-controlled, privacy-preserved management of digital identities. DID empowers professionals by placing control of identity directly in the hands of individuals. Through the application of zero-knowledge proofs (ZKPs), DIDs allow individuals to authenticate the legitimacy of their credentials while keeping their personal data confidential.
The Problem with Fake Profiles in Professional Networks
These profiles manifest in various forms, from entirely fabricated personas to those that falsely represent an individual’s credentials, affiliations, or experiences. These deceptive entities do more than just mimic legitimate users, leading to issues like identity theft, social engineering, and phishing attacks—they also compromise the integrity and security of entire organizations.
Beyond individual risks, these fake profiles can distort the job market by misrepresenting skills and qualifications, potentially leading to the hiring of unqualified candidates or the exclusion of deserving professionals.
A study reveals that fake accounts cause substantial financial damage, costing businesses millions annually. Specifically, in the financial services sector, identity fraud from such activities can lead to average losses ranging between $81,000 and $97,000 per incident.
Further compounding the issue, the Federal Trade Commission (FTC) reported consumer losses exceeding $1.9 billion in 2019, much of which was tied to employment scams that leveraged stolen personal information.
The rise of sophisticated AI tools has further exacerbated this issue and has made it easier for malicious actors to create convincing fake profiles.
Identifying the Role of Decentralized Identity in Professional Networks
The first step in combating fake profiles is to effectively identify and verify the authenticity of users on professional networking platforms. Current traditional identity verification processes are often inadequate, relying solely on email verification or connecting with existing social media accounts.
These centralized systems rely on centralized authorities to verify and manage user identities, creating a single point of failure and making them vulnerable to data breaches, identity theft, and other security risks. These methods can be easily manipulated, allowing fake profiles to slip through the cracks.
As professional networks struggle with the rising tide of fake profiles, innovative solutions like Define Protocol are emerging, promising to redefine how we ensure authenticity and security in digital identities through decentralized identity management. The role of decentralized identity in professional networks is becoming increasingly crucial in this fight against fraudulent accounts.
Why Decentralized Identity is the Solution
Decentralized identity provides a promising solution to the problem of fake profiles. Decentralized identity management is a way of managing your online identity where you, the user, have control over your own personal information, rather than having it controlled by a central organization or company. The role of decentralized identity in professional networks is central to this shift in control and security.
Importance of Decentralized Identity in Professional Networks
While traditional identity verification methods have their limitations, emerging decentralized solutions offer a glimpse into a more secure future, as envisioned by initiatives like Define Protocol.
- If an organization like a university or training program is issuing credentials, they can do so securely by making credentials fraud-proof. This avoids many risks for companies and impacts people’s safety, as many people who get fake credentials work in health care or do more risky field work operating heavy machinery.
- Allows organizations to verify information without having to contact the issuing party, like a driver’s licensing organization or university for example, to ensure that IDs, certificates, or documents are valid. Traditional, manual verification processes take weeks to months which slows down recruitment and processing times while using a lot of financial and human resources.
As we confront the persistent challenge of fake profiles on professional networks, it’s clear that traditional security measures are no longer sufficient. The root cause often lies in financial scams, data breaches, and social engineering tactics that exploit centralized systems. The true breakthrough is recognizing that identity must be owned by the individual, not managed by centralized entities. Decentralized identity technology empowers users to control their digital identities securely and privately. This approach not only protects against fraud but also fosters genuine trust and transparency in professional interactions.
Romil Verma, CEO of Define Protocol. Stanford Graduate, Previously at Google.
How Does Decentralized Identity (DID) Work?
The current systems of user identification on platforms are centralized. As a counter, the World Wide Web Consortium (W3C) recommended a Decentralized Identifier (DID) as an official Web standard.
Decentralized Identifiers not only verify human authenticity but also staunchly protect user privacy and data ownership. It employs zero-knowledge proofs (zk-SNARKs) to validate credentials without revealing the underlying data. This means that while the authenticity of the credentials can be verified, the specific details remain confidential, protecting user privacy.
Understanding the Implementation of DID: An Illustration
The key aspects of decentralized identity are:
- Decentralized Control
- Verification and Privacy
- Blockchain Integration
- Interoperability
Now, the implementation of Decentralized Identifiers (DID) in professional networks can be elucidated through an example of the Define DID–
Step 1: Creating a DID
Define DID acts as proof of personhood, certifying that each profile corresponds to a real, unique individual. You begin by creating your unique Define DID by submitting basic information. This DID is then registered on a blockchain, securely linking it to your identity without the need for central oversight. The role of decentralized identity in professional networks starts with this initial creation of a secure and unique identity.
Step 2: Adding Credentials
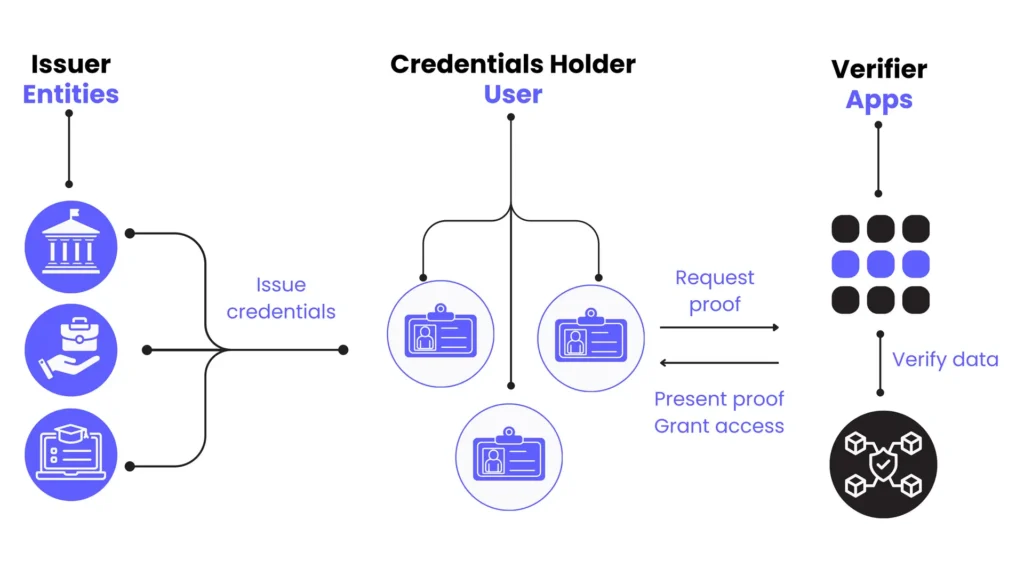
It’s easy for users to fabricate educational qualifications, skills, and work history on their profiles. However, Define credentials are verified and signed by reputable entities and stored on the blockchain, making them immutable and reliable.
You can add your credentials, such as work history, education, and skills. Each of these credentials is verified by trusted entities. For instance, your university issues a digital certificate directly linked to your Define DID, confirming the degree.
The image below perfectly illustrates the explanation of how credentials are added and verified—
Step 3: Privacy-Preserving Verification
When applying for jobs, you can prove your qualifications using zero-knowledge proofs to demonstrate the authenticity of your credentials to potential employers without revealing the actual documents or specific details.
Step 4: Control and Consent
Throughout this process, you retain full control over who can access her information and to what extent. You can give temporary access to your profile for a job application and revoke it once the process is completed. The role of decentralized identity in professional networks is crucial in maintaining this control and consent over personal data.
Step 5: Interoperability
Define DIDs are not confined to any specific platform, enabling you to maintain control over your digital identity across different services. Thanks to their interoperable nature, you can utilize the same identity across various networks that support the DID standard, streamlining interactions and eliminating the need to repeatedly verify your identity.
This role of decentralized identity in professional networks ensures seamless integration and functionality across different platforms.
The Future of Professional Identity
In the future, professionals will have full ownership and control over their digital identities, eliminating the need for third-party intermediaries or data silos. The role of decentralized identity in professional networks will become the norm, allowing individuals to securely and selectively share verified credentials and information with potential employers, clients, or business partners.
Professional networks and platforms will likely integrate decentralized identity solutions, enabling seamless verification of credentials, work histories, and reputations. This will not only combat fake profiles but also streamline the recruitment and hiring processes, ensuring that candidates are accurately represented and evaluated based on their true qualifications and achievements. The role of decentralized identity in professional networks will be integral in achieving this future vision.
Individuals could form decentralized autonomous organizations (DAOs) or guilds based on shared interests, skills, or industries, leveraging the power of decentralized identity to establish trust and facilitate seamless collaboration.
By putting individuals in control of their digital identities and enabling secure, verifiable, and portable professional credentials, decentralized identity solutions like Define Protocol’s DID could reshape the future of professional networking and identity management. The role of decentralized identity in professional networks is set to revolutionize how we perceive and manage digital identities, making the online professional environment safer and more trustworthy.