Even though the cryptocurrency industry has only recently gone mainstream over the past decade, protecting cryptocurrencies from malicious hacks has almost become synonymous within the community. Therefore, shrewd investors should know the safest ways to use their crypto hot wallets to protect their investments.
- Types of Crypto Hot Wallets
- Why Is It Critical to Be Vigilant When Holding Assets in a Hot Wallet?
- Best Practices for Storing Cryptocurrencies on a Hot Wallet
- Use a Reputable Cryptocurrency Exchange
- Use a Strong Password and Change It Frequently
- Never Share the Private Key and Seed Phrase
- Avoid using Public WiFi
- Beware of Phishing Scams
- Conclusion
While there are vulnerabilities associated with transacting with crypto hot wallets online, basic risk management such as never sharing private keys, avoiding public WiFi while transacting, recognizing phishing scams, using a strong password, and using reputable crypto exchanges are vital.
Types of Crypto Hot Wallets
Custodial Hot Wallets or Exchange Wallets
These are web-based exchange wallets where the ownership of one’s private keys (which effectively equates to a password in crypto land to a user’s funds on the blockchain) lies in the hands of a third party or centralized party. Examples of such wallets include cryptocurrency exchange platforms such as Binance, Coinbase, and many more. Using a custodial wallet involves having complete trust in a third party This is akin to the trust placed in traditional bank accounts to store funds. Despite the convenience attached to this method of holding funds, it goes against the philosophy behind bitcoin and other cryptocurrencies.
Non-Custodial Crypto Hot Wallets
True self-custody is made possible by these wallets, giving users control over their private keys and, by extension, their cryptocurrency holdings. Non-custodial crypto hot wallets give people the freedom to be their own bankers. However, this freedom also comes with the added responsibility of taking complete ownership of protecting their assets by themselves. There are no middlemen to help recover lost funds. MetaMask, Trust Wallet, Phantom wallet, and Exodus are well-known non-custodial crypto hot wallets.
Why Is It Critical to Be Vigilant When Holding Assets in a Hot Wallet?
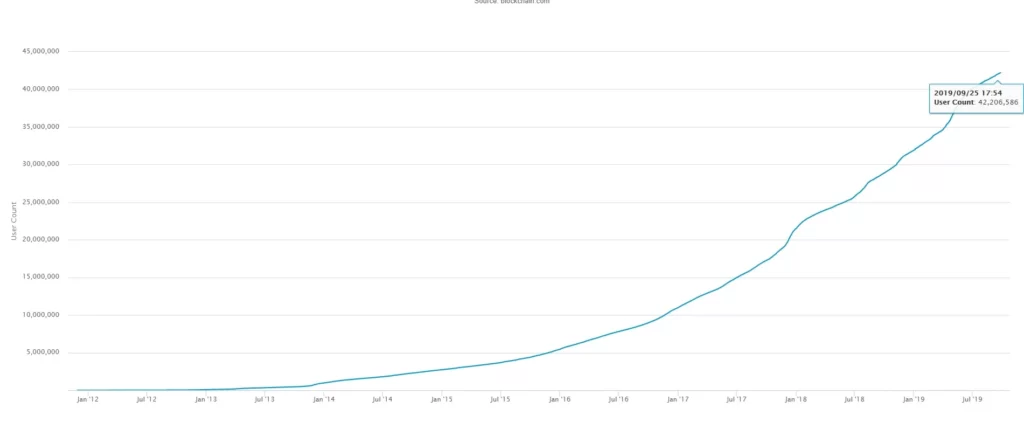
Since hot wallets connect to the internet, they have an advantage over cold wallets in that transactions can be completed on the go almost instantly with a seamless user experience. However, while this is ideal for newbie enthusiasts, the growing popularity of cryptocurrencies has also increased threats to the ecosystem. This makes it highly lucrative for attackers.
A cumulative amount of nearly USD $2.72 Billion has been stolen from crypto exchanges since 2012.
HedgewithCrypto
In addition to high-profile exchange hacks, the crypto ecosystem has experienced numerous non-custodial crypto wallet vulnerabilities. Crypto hot wallets based on the Solana blockchain were subject to the latest victim of crypto theft. The attack impacted popular hot wallets like Phantom, Slope, and TrustWallet.
The widespread hack is estimated to have impacted more than 7,000 wallets and resulted in $8 million in funds lost.
Coinbase
Best Practices for Storing Cryptocurrencies on a Hot Wallet
Use a Reputable Cryptocurrency Exchange
If choosing to park assets on an exchange, understanding that some platforms are more secure than others is critical. Tier 1 exchanges are usually established entities with good security measures in place. Researching past breaches and the security features available on a preferred exchange becomes paramount.
Most cryptocurrency exchanges do not have the legal obligation to safeguard their users’ cryptocurrency investments in the event of a cyberattack. This could result in the user losing all of their holdings. Hence, it is essential to select an exchange that uses security best practices, such as requiring multi-factor authentication (MFA) and address whitelisting.
Use a Strong Password and Change It Frequently
As is the case with anything online that discloses sensitive information, it is always advisable to protect passwords diligently. While this has been reiterated by cyber security specialists. Astonishingly, according to a recent study by NordVPN, the most common password of 2022 is, you guessed it, password. Maintaining best practices when choosing a password for a crypto wallet includes making sure the password is complex, avoiding password reuse, avoiding using personal information in the password, and changing the password regularly.
Never Share the Private Key and Seed Phrase
As the name suggests, private keys are intended to be kept confidential and only accessible by the user. Similarly, the recovery seed phrase needed to back up a cryptocurrency wallet on a new device needs to be kept in a secure location. Anyone with knowledge of the private key or seed phrase has total control over the user’s assets.
Avoid using Public WiFi
It is not advisable to use public internet connections to access a hot wallet. Most public WiFi networks are not encrypted, making them plain sailing targets for attackers to access remotely. Furthermore, using VPNs (Virtual Private Networks) to hide IP addresses and locations keeps one’s online activity private and secure. This gives them control over their data, away from potential eavesdropping cyber thieves.
Beware of Phishing Scams
In a phishing attack, hackers attempt to deceive individuals into providing their user credentials or private key information on a website that appears legitimate. It is not advisable to trust texts, emails, or chat links from social media platforms that ask for personal information. Awareness of potentially malicious websites and links is crucial, and research on the steps to bypass such ruses is vital.
Conclusion
All online transactions can be susceptible to vulnerabilities. Therefore, ensuring that these best practices are maintained will enhance the likelihood of securing your crypto hot wallets. While this can seem intimidating, taking additional precautionary measures to safeguard your crypto hot wallets and assets is undoubtedly worthwhile, for this space is still in its infancy, and the growth potential is infinite.