Modularity appears to be the newfound implementation by developers to future-proof blockchain protocols. Among the layers making up this modular architecture, data availability layers (DALs) are at the heart of this architectural innovation.
As blockchains continue to grapple with scalability issues, DA layers come to offer a specialized solution by offloading the responsibility of data availability from the main execution layer.
Not all DA layers are created equal.
Among the many data availability solutions out there, four projects are leading the narrative:
- Celestia
- Eigen DA
- NEAR DA
- Avail
This article explores the four top Data Availability layers and offers developers a clearer picture for choosing the best data layer for their dApps.
A Recap of Data Availability
In a peer-to-peer ecosystem like DLT-based networks, a transaction is as good as non-existent if it cannot be seen and/or verified by other peers in the network.
Blockchain networks are meant to be trustless — this means that every transaction in a blockchain should be verifiable and only then can it be deemed legitimate. No entity, however powerful or “trustworthy”, should have the ability to successfully broadcast a transaction to the network and include it in the chain without verifiable proof.
Data availability is the property of decentralized P2P networks that guarantees network security and integrity by ensuring all transaction data is readily available for all participants at any time.
When data is not readily available, it can lead to vulnerabilities, such as data withholding attacks, which undermine the trust and functionality of the system. Effective DA layers address these challenges by ensuring that data is consistently available, verifiable, and retrievable, thereby enhancing the overall performance and reliability of the blockchain.
Hence, data availability is the backbone for:
- Accessibility
- Transparency
- Immutability
Traditionally, data availability is ensured by every node in the blockchain having to download the entire history of the network. Over time, new solutions emerged that are more efficient and practical.
How To Choose A Data Availability Layer: Key Evaluation Criteria
We’ve established that not all DA layers are built the same. Each has its unique implementation and developers must choose what works best for their dApp. There are several criteria to evaluate, and three key ones are:
- Data replication and storage
- Networking and consensus mechanism
- Incentivization mechanism
- Data Replication and Storage
A blockchain is basically a network of nodes constantly talking to each other and consenting (or rejecting) newly broadcasted transactions. These nodes store transaction data to ensure availability for verification and other operations.
Learn more about blockchain ETL data pipelines with this dedicated article.
The way these nodes store blockchain data is not universal. Some keep the entire record, some keep partial data (using which the rest can be reconstructed), and others may employ erasure encoding technology.
Data replication refers to the number of times the data copied and stored across the network. A higher replication factor increases redundancy and data availability but can also lead to higher storage costs and potential network congestion.
- Full Replication: This is the traditional approach where every node stores a complete copy of the blockchain’s data. It provides the highest level of security and data availability, as any node can independently verify the entire history of transactions. However, it can be quite resource-intensive, especially as the blockchain grows in size.
- Partial Replication (Sharding): Here, the blockchain is split into smaller partitions called shards (like NEAR). Each node only stores the data for a specific shard, reducing the storage requirements significantly. However, it requires complex coordination mechanisms to ensure data consistency and availability across shards.
- Erasure Coding: This technique splits data into fragments and adds redundant parity data. Even if some fragments are lost, the original data can be reconstructed using the remaining fragments and parity data. This offers a good balance between storage efficiency and data availability, as it requires less storage than full replication while still providing redundancy.
- Network Topology and Consensus Mechanism
Network topology refers to the arrangement and structure of connections between nodes. Common topologies include structured networks (like trees or rings), unstructured networks (like gossip protocols), and hybrid approaches.
That and the consensus mechanism used are fundamental to the operation of a DAL. They determine how nodes communicate, reach agreement on data validity, and ensure data availability.
While the network topology affects efficiency and scalability, the consensus mechanism affects cost and decentralization (and security).
Proof of Stake (PoS) is among the most widely used consensus mechanisms in newer blockchains (after Bitcoin), and consequently, their inherent data layers. Proof of Replication (PoRep) is another popular type of consensus mechanism that is specific to storage-based networks.
- Incentivization Mechanism
A good incentivization mechanism is critical to achieve active participation by the community members. Active participation directly correlates to reliable data storage (through redundancy, node uptime, etc.) and availability.
There are mainly three ways participating members are rewards:
- Block rewards
- Transactions fees
- Grants
Another (less common) incentivization mechanism is the use of reputation systems. Some DALs use reputation systems to track the performance and reliability of node operators, with higher reputation leading to increased rewards. The downside to this is that it introduces a degree of trust (based on reputation) in the system, which goes against the principles of decentralization.
Higher rewards is not all that would incentivize participation. The slashing mechanism should also be particularly reasonable.
Slashing is a penalty mechanism that reduces or confiscates a portion of a node operator’s stake if they engage in malicious or negligent behavior, like broadcasting fake transactions, going offline for extended periods, or failing to provide data when requested. Yet, the slashing mechanism must be reasonable to accommodate for any unintentional incorrect broadcasts.
Unintentional wrong transaction broadcasts are more common than most people assume.
For example, network issues like latency, packet loss, or disconnections can disrupt communication, causing nodes to have different views of the blockchain’s state and potentially broadcast conflicting transactions.
Therefore, a slashing mechanism should strike a balance between deterring malicious actors and accommodating occasional unintentional slashes by not being too harsh.
Overview of the Data Availability Layers for Rollups
While there are separate projects dedicated to innovating data availability as a layer, no standalone blockchain exists without inherent data availability mechanisms. So, let’s look at how Ethereum natively addresses data availability on the mainnet before exploring other solutions.
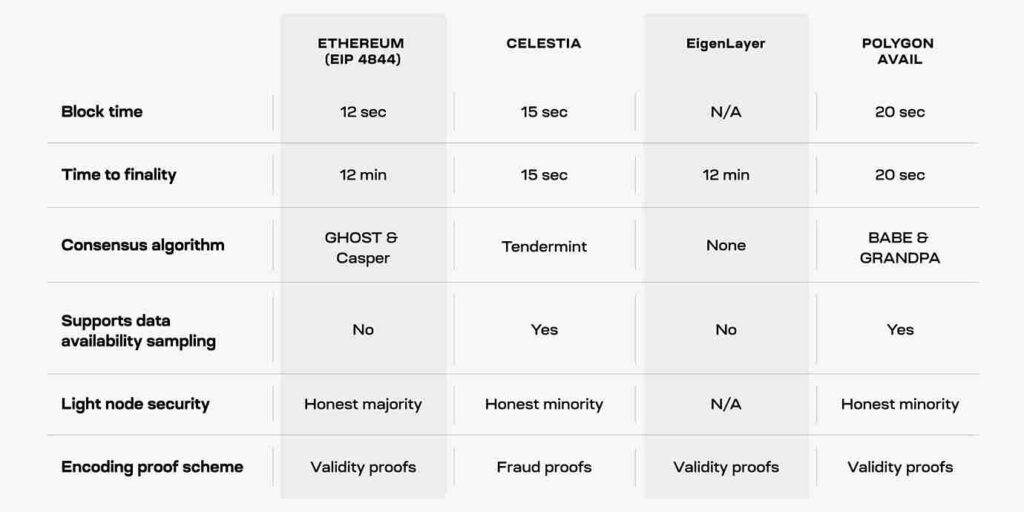
1. Ethereum DA
Modularity in blockchains is a relatively new concept. Therefore, the biggest difference in Ethereum DA from others discussed in this article is its coupled nature.
In Ethereum, data availability is tightly coupled with the execution layer. Every full node in the network is responsible for downloading, storing, and verifying every piece of data included in each block.
Such a monolithic approach requires large storage and more computing power. As the blockchain grows, the cost of operating a node increases and, if the trend continues indefinitely, only corporations would have the pockets to run a full node.
To mitigate these hurdles, the Ethereum community has been hard at work in coming up with unique DA solutions that would additionally complement Ethereum’s stateless future. The most recent and laudable innovation is the implementation of EIP-4844 (Proto-Danksharding).
EIP-4844 introduces “blob-carrying transactions” that can carry large amounts of data specifically for rollups. This increases data capacity, reduces costs, and improves scalability, paving the way for full Danksharding in the future.
2. Celestia
Celestia’s strength lies in its modular architecture that separates execution, consensus, settlement, and data availability. This separation lets each component be specialized and optimized, significantly enhancing the overall efficiency and scalability of the network.
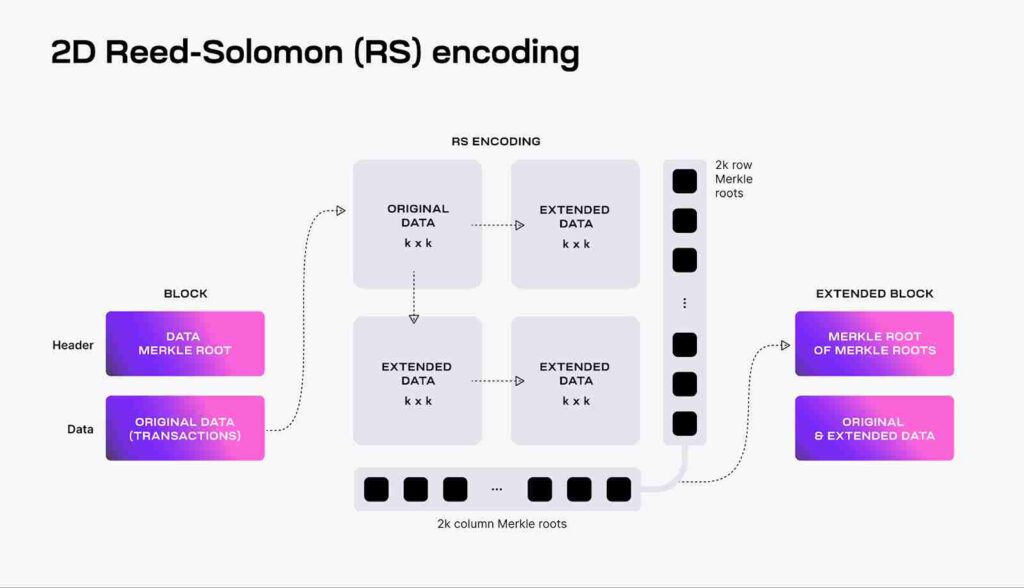
Celestia employs Data Availability Sampling (DAS) made possible by 2D RS encoding, enabling light nodes to verify the availability of data without the need to download the entire blockchain history. This method involves light nodes randomly sampling portions of block data that would then allow the network to scale DA without a corresponding increase in node requirements.
Another crucial feature is the use of Namespace Merkle Trees (NMTs), which segregate block data into distinct namespaces. This approach means that applications only need to process data relevant to them, thereby reducing the overall data processing load.
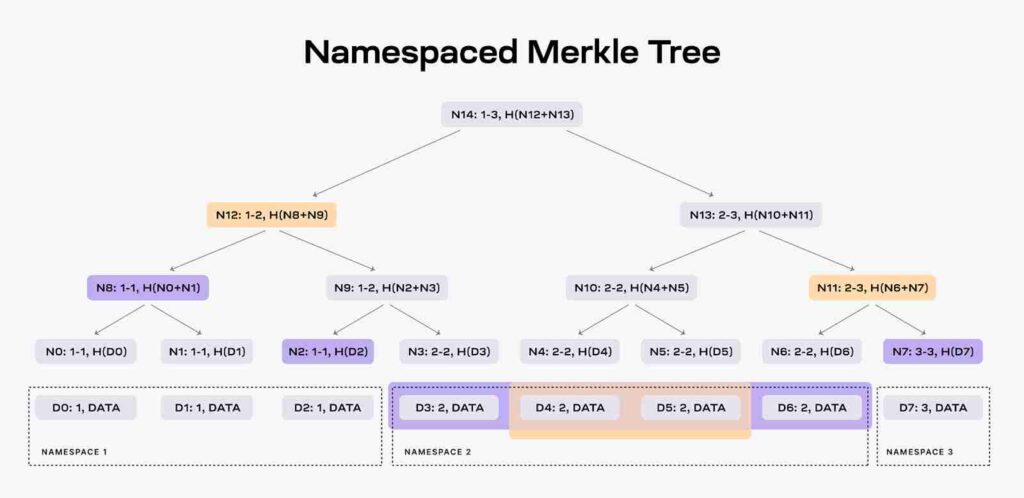
3. EigenDA
EigenDA, a component of EigenLayer utilizes Ethereum’s security architecture via node re-staking resulting in more affordable and high-throughput data availability services.
The technical foundation of EigenDA is in line with Ethereum’s Danksharding path, utilizing technologies such as erasure coding, KZG commitments, and Authenticated Coded Dispersal (ACeD).
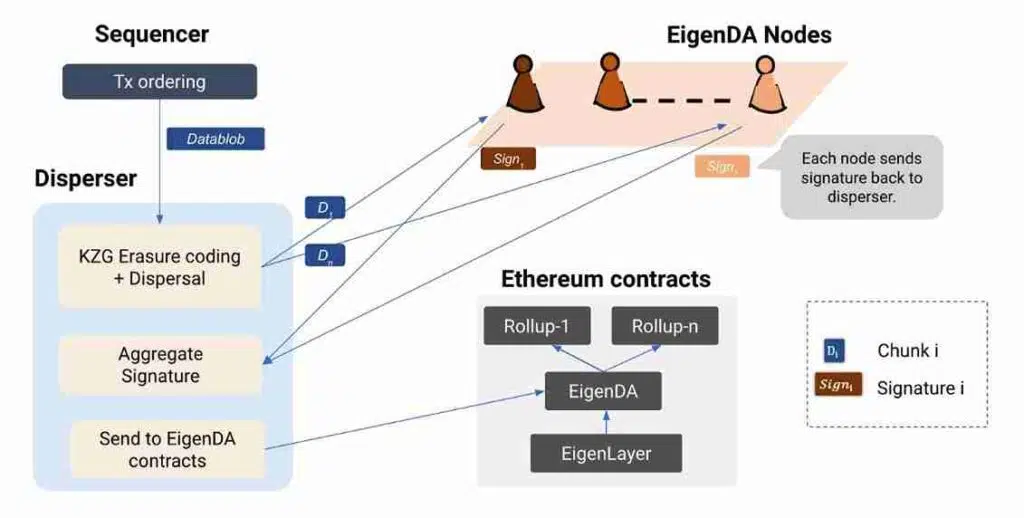
The finality time of EigenDA is dependent on the Ethereum block time — between 12 and 15 minutes.
4. NEAR DA
NEAR Protocol’s DA solution emphasizes scalability and decentralization through the use of sharding technology and stateless validation. This approach simplifies data management for L2 projects by distributing data across multiple shards and allowing nodes to process transactions without needing to store the entire state.
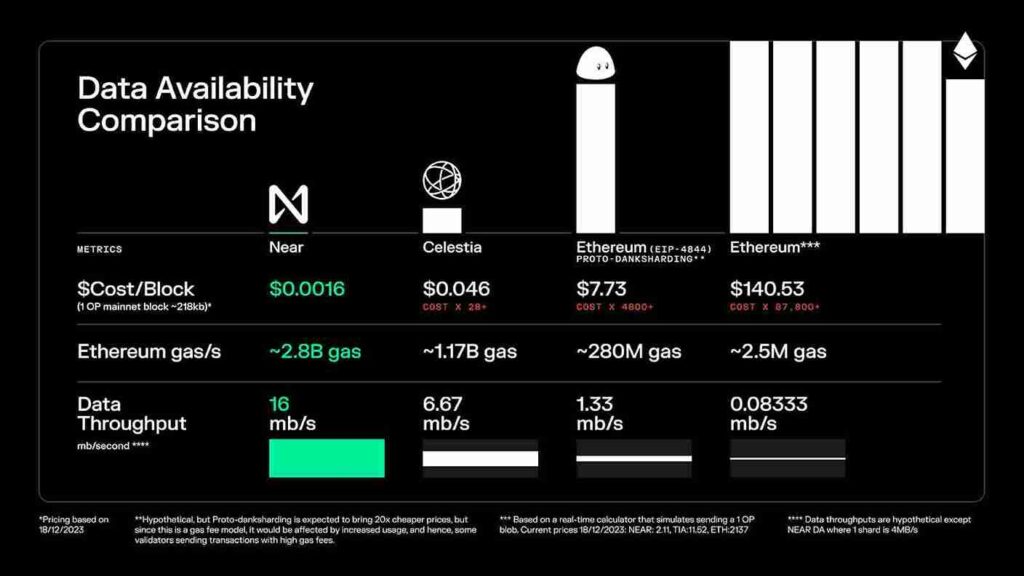
Through the use of sharding, NEAR’s network is able to handle a higher amount of transactions in parallel, which lowers latency and improves throughput.
Because stateless validation eliminates the requirement for individual nodes to keep an exhaustive record of the blockchain’s state, it further eases the load on them and makes data processing and storage more effective.
5. Avail DA
Avail, once a part of Polygon, focuses on optimizing blockchain data processing and storage through a modular architecture. It permits asynchronous interactions between application chains, which improves network performance and makes it possible for light clients to efficiently check data integrity.
Since consensus and data availability are kept apart in Avail’s architecture, specific optimization is possible at every tier. By separating the two, the network can scale effectively and still maintain strong security and data availability standards.
Light clients in the Avail network can verify data availability through sampling methods similar to those used by Celestia, providing a trust-minimized environment.
By enabling efficient data verification and processing, Avail aims to improve the user-friendliness and scalability of blockchain applications. Its modular design supports the development of specialized application chains, which can interact asynchronously, further enhancing the overall performance of the network.
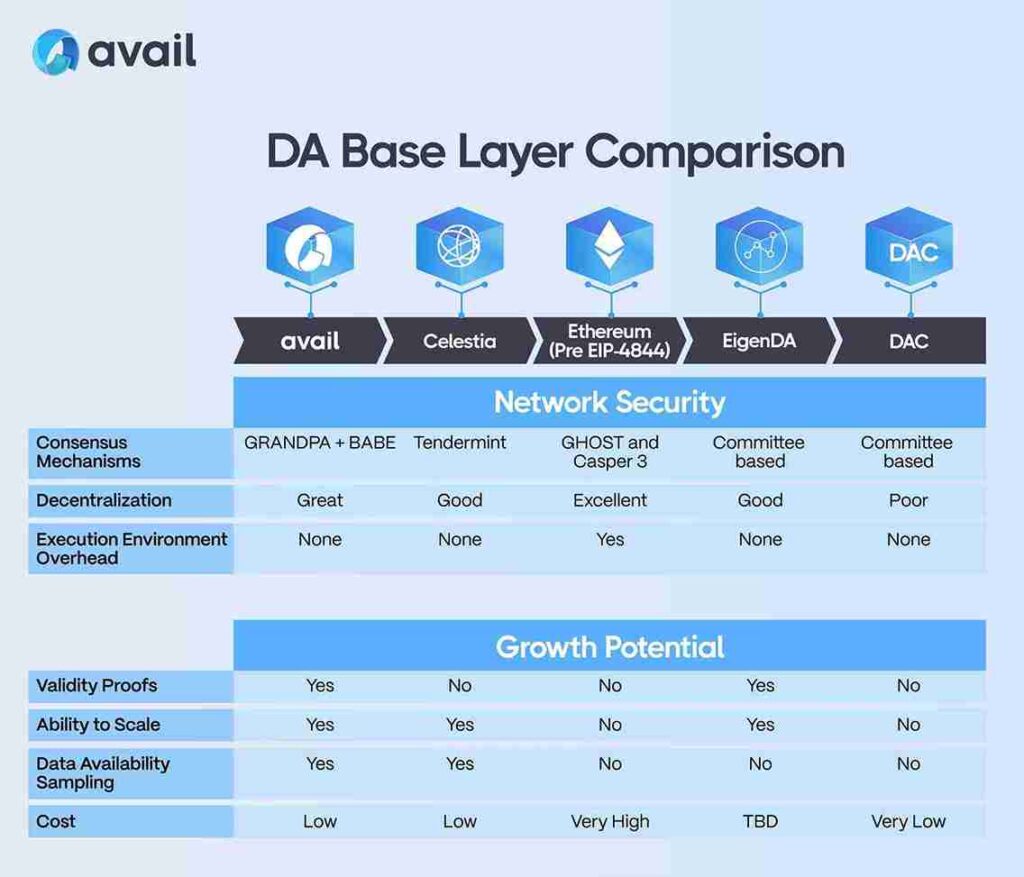
Comparison of DA Layers
| Feature | Celestia | EigenDA | NEAR DA | Avail DA |
| USP | Modular blockchain, specialized DA layer | DA layer (not a blockchain) built on Ethereum | DA solution for Near Protocol | Scalable DA for rollups |
| Data Availability Mechanism | Namespaced Merkle Trees (NMTs) | Reed-Solomon erasure coding | Sharding (Nightshade) | DAS, KZG commitments |
| Encoding Proof Scheme | Fraud proofs for incorrectly encoded data | KZG commitments for validity proofs | Validity proofs | Validity proofs |
| Node Requirements | Light nodes verify data with low requirements, full nodes handle broadcasting and consensus | Lower operational costs, nodes verify small data shards using KZG commitments | Nodes do not need to store entire state due to stateless validation | Light clients verify data with minimal requirements |
| Consensus Mechanism | Tendermint | Inherits Ethereum’s PoS | Thresholded Proof-of-Stake (TPoS) | BABE and GRANDPA |
| Scalability | High (due to DAS) | Limited by Ethereum base layer | High (due to sharding) | High (optimized for rollups) |
| Ethereum Compatibility | Requires bridges/interoperability solutions | Native compatibility | Requires bridges/interoperability solutions | Flexible (can be used with various chains) |
| Security | Relies on Celestia’s PoS and fraud proofs | Inherits Ethereum’s security | Relies on Near’s TPoS and fraud proofs | Depends on underlying blockchain’s security |
| Cost | Minimal fees | Potentially high (due to Ethereum gas fees) | Relatively low | Minimal overhead |
Conclusion
The DAL you choose isn’t just a technical decision; it’s a strategic one. It molds your dApp’s economic model, its security guarantees, and even the types of users it can attract.
- Celestia-based dApps might be great where data richness and complex computation are most important — think decentralized social networks.
- EigenDA could be the go-to for DeFi protocols seeking robust security inherited from Ethereum while still aiming for cost efficiency.
- NEAR DA caters to those building highly interactive dApps, where responsiveness and real-time data are non-negotiable.
- Avail’s flexibility is ideal for teams experimenting with novel architectures or bridging multiple ecosystems.
Over time, we can expect these innovations to lower the cost of using rollups on Ethereum.